The NCCC experts conducted a two-day course “Network Test for Vulnerabilities and Ethical Hacking” for representatives of key cybersecurity and critical infrastructure actors
Experts of the National Coordination Center for Cybersecurity in cooperation with CRDF Global in Ukraine and with the support of the U.S. Department of State conducted a two-day course “Network Test for Vulnerability and Ethical Hacking” prepared by Purdue University (the U.S.) for key cybersecurity and critical infrastructure actors.
On the first day of the event, the theoretical module was presented by Purdue University professors, practitioners and certified professionals with many years of experience in cybersecurity, who won prizes in world-famous hackathons – Jeremy Rasmussen, Michael Malen, Barrett Darnell. They also mentored the practical part of the training.
The training included pentest planning, open-source intelligence (OSINT), post-attack techniques and algorithms, and digital forensics.
During the practical exercises (CTF) the participants of the event looked for flags in three types of competitions:
enemy TTP analysis – simulation of tactics, methods, and procedures necessary to detect the activities of “hostile agents” in the internal network through the analysis of captured logs of network traffic;
tunneling – a series of tasks in which participants have access to a secure shell (SSH) of a computer connected to multiple internal networks. Players used different SSH tunneling techniques to access different subnets and run malicious codes after gaining access to the machines.
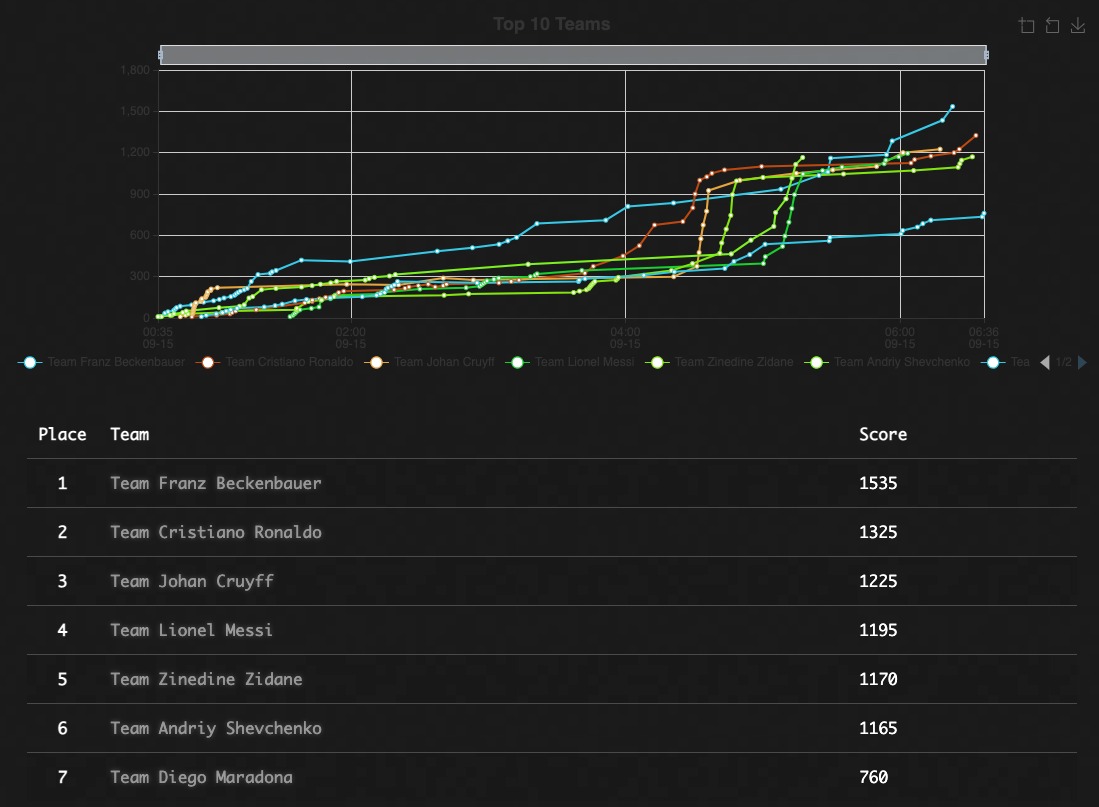 The Beanie Baby series of challenges contained a web application that was vulnerable to SQL injection, and players had to gain remote access to the shell on the server and pass on their privileges to various Linux users by running vulnerable code.
The Beanie Baby series of challenges contained a web application that was vulnerable to SQL injection, and players had to gain remote access to the shell on the server and pass on their privileges to various Linux users by running vulnerable code.
This time the mentors named the teams in honor of famous players from different countries and gathered the players so that each team had specialists with different levels of professional skills, so all teams had an equal chance to win.
The team of cybersecurity experts from the SSU, the National Bank of Ukraine, the Cyberpolice, the Ministry of Defense of Ukraine, the General Staff of the Armed Forces of Ukraine, and the State Border Guard Service of Ukraine became winners.